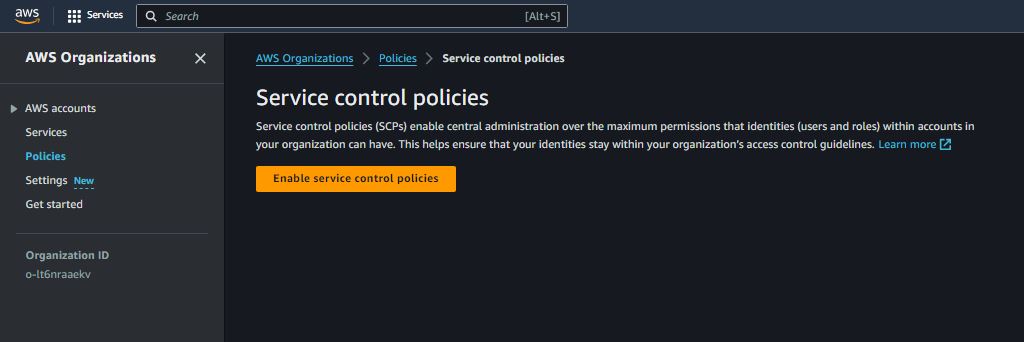
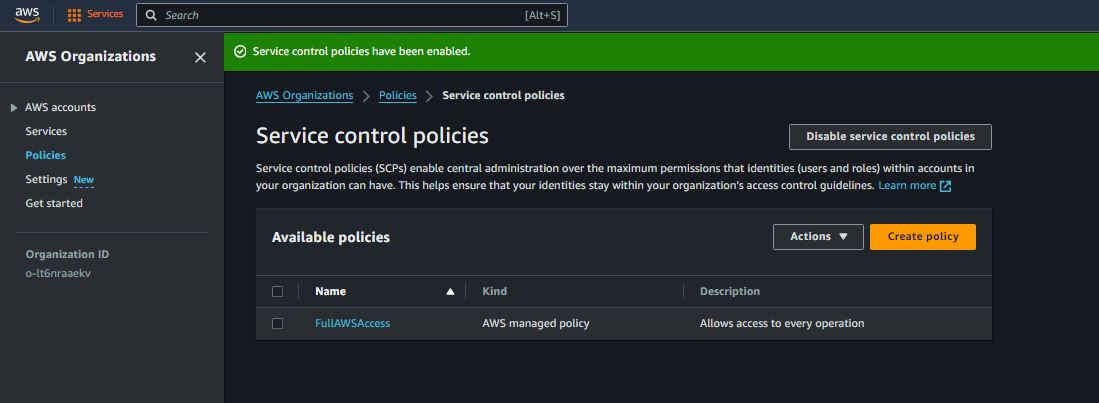
AWS Organization & Service Control Policies (SCPs)
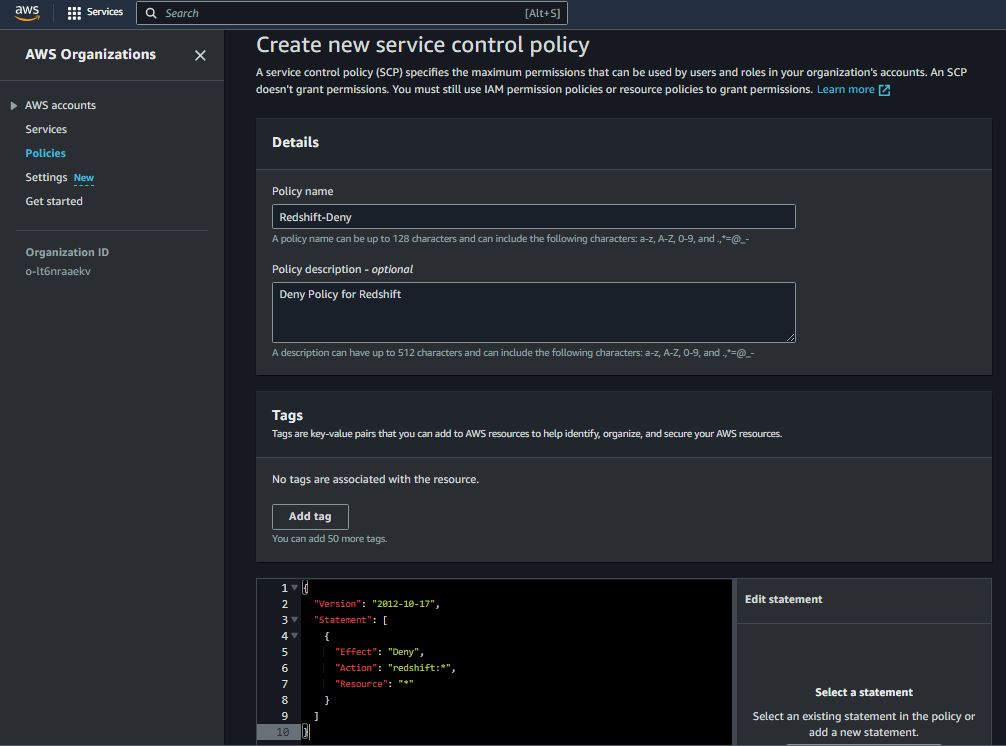
Deny Access to Specific Service
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "redshift:*",
"Resource": "*"
}
]
}
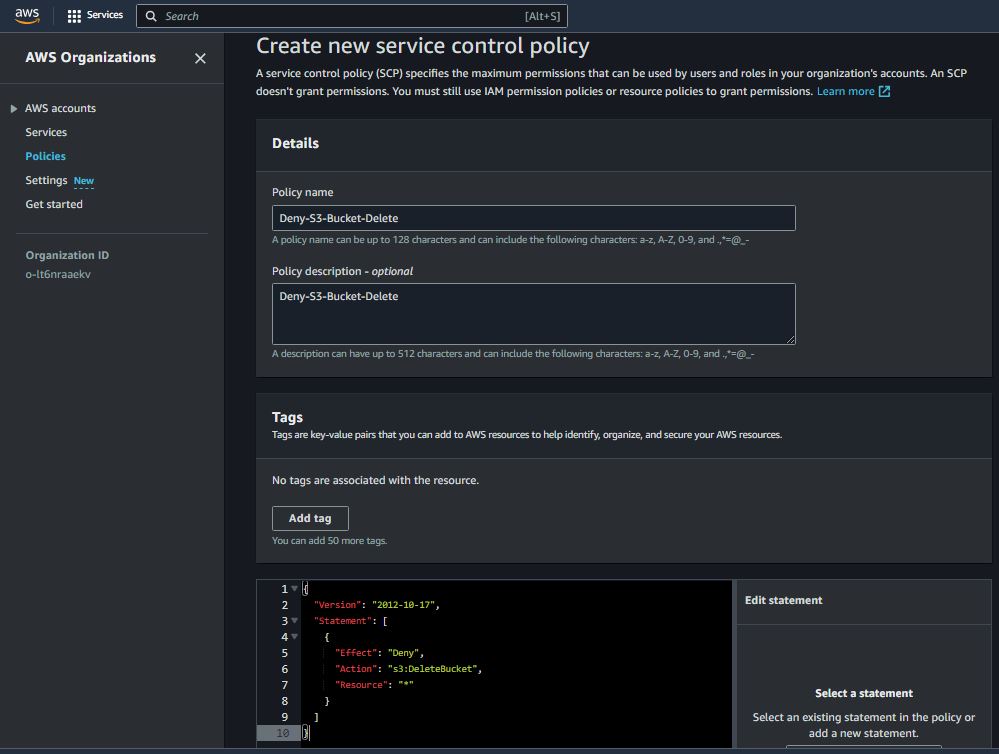
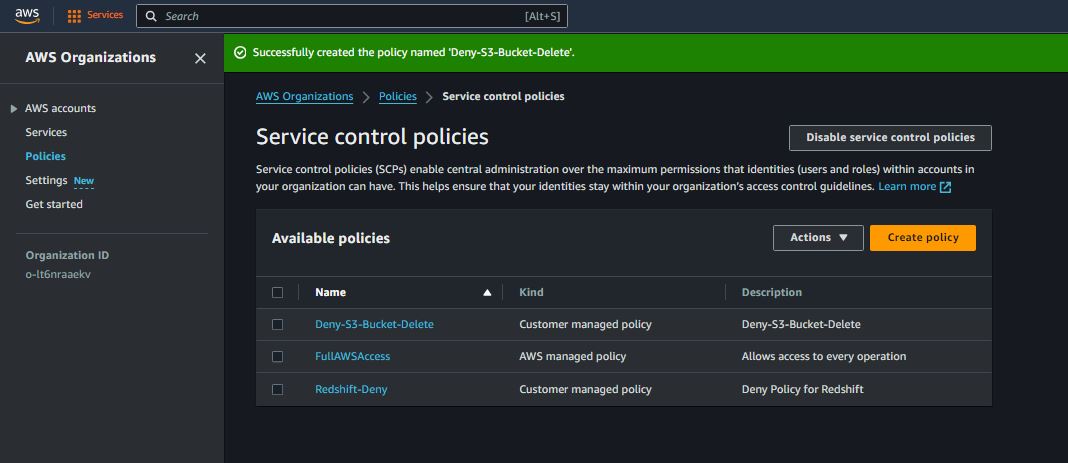
Deny Specific Actions
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "s3:DeleteBucket",
"Resource": "*"
}
]
}
Deny Access Based on Conditions
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "ec2:*",
"Resource": "*",
"Condition": {
"NotIpAddress": {
"aws:SourceIp": [
"203.0.113.0/24"
]
}
}
}
]
}
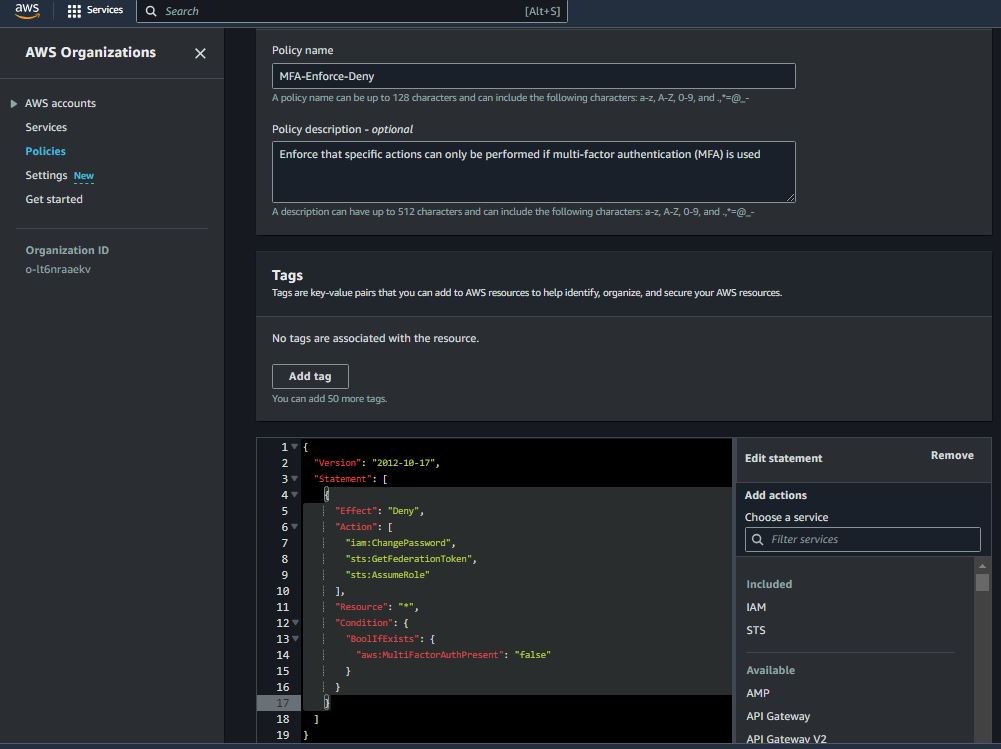
Require MFA for Certain Actions
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": [
"iam:ChangePassword",
"sts:GetFederationToken",
"sts:AssumeRole"
],
"Resource": "*",
"Condition": {
"BoolIfExists": {
"aws:MultiFactorAuthPresent": "false"
}
}
}
]
}
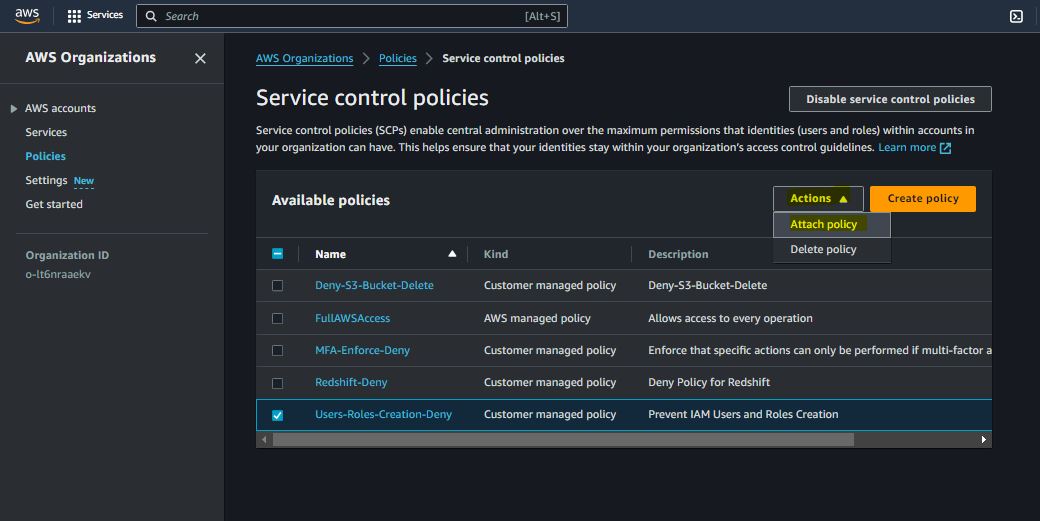
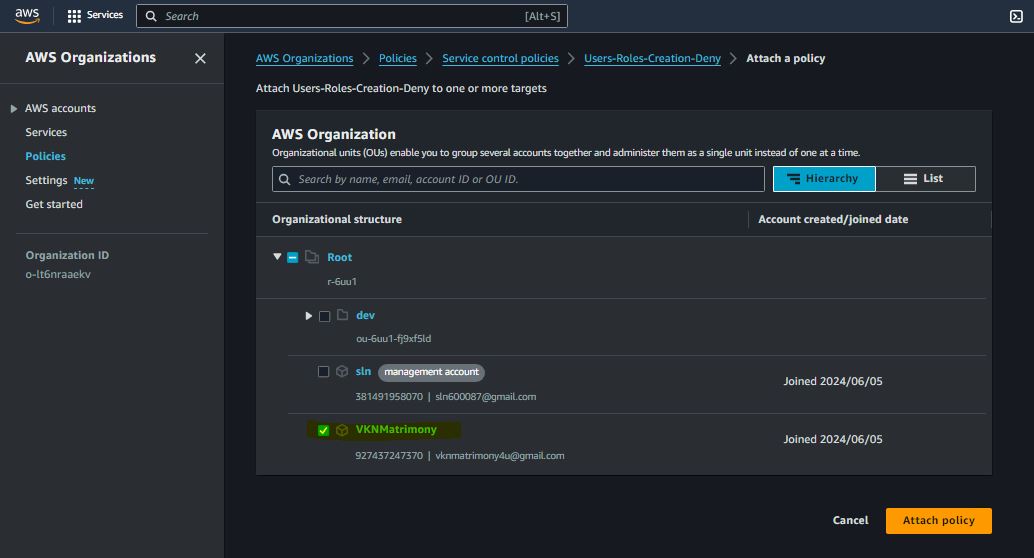
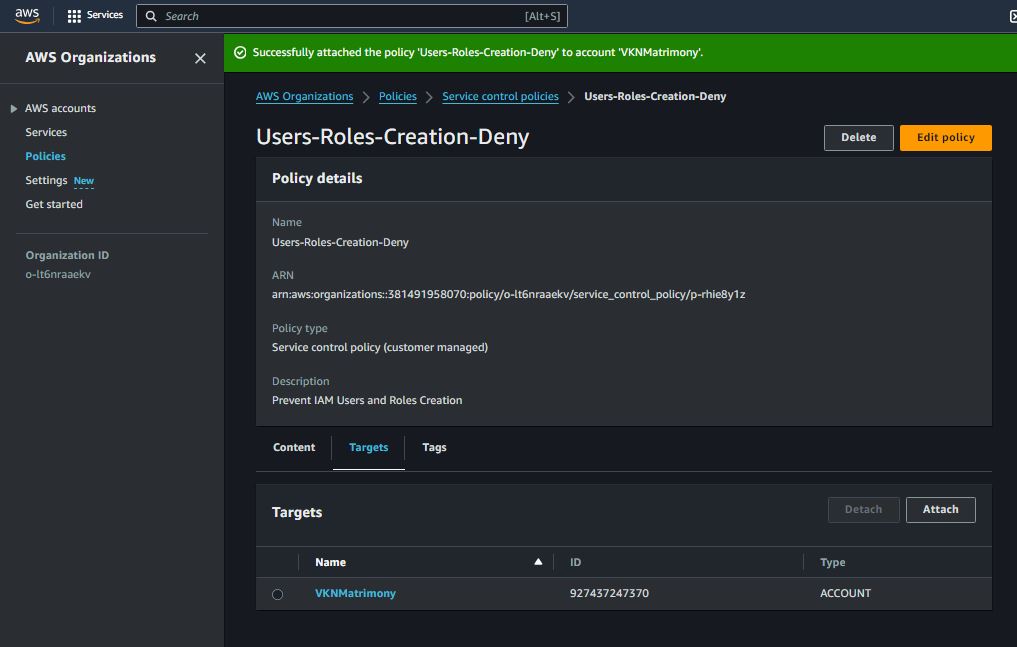
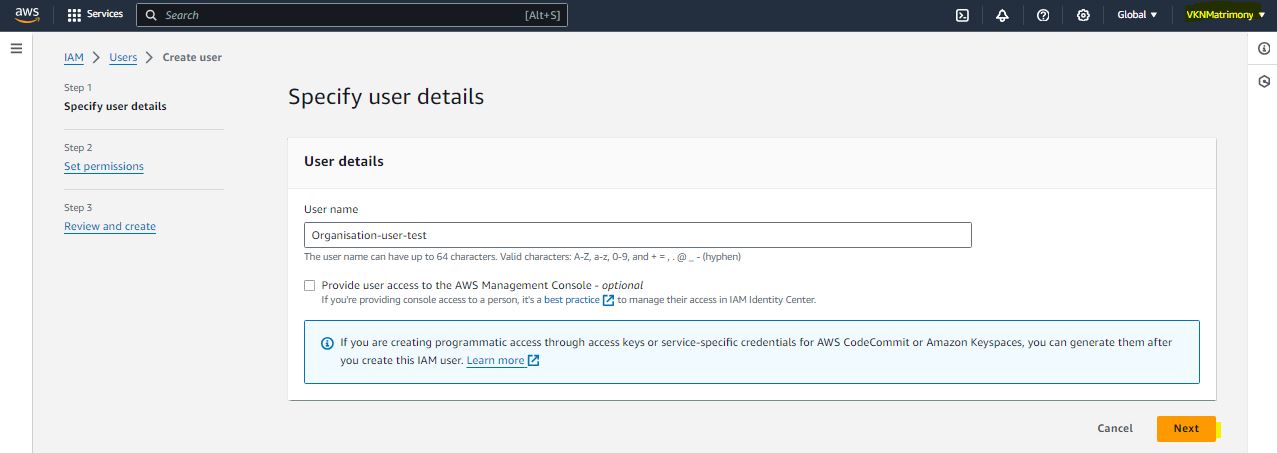
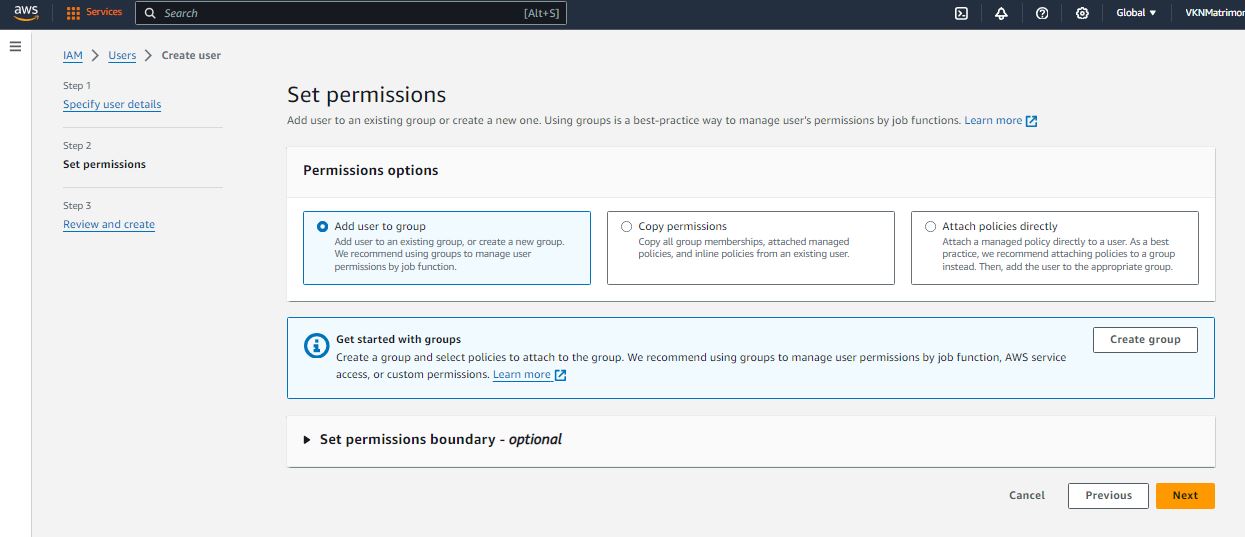
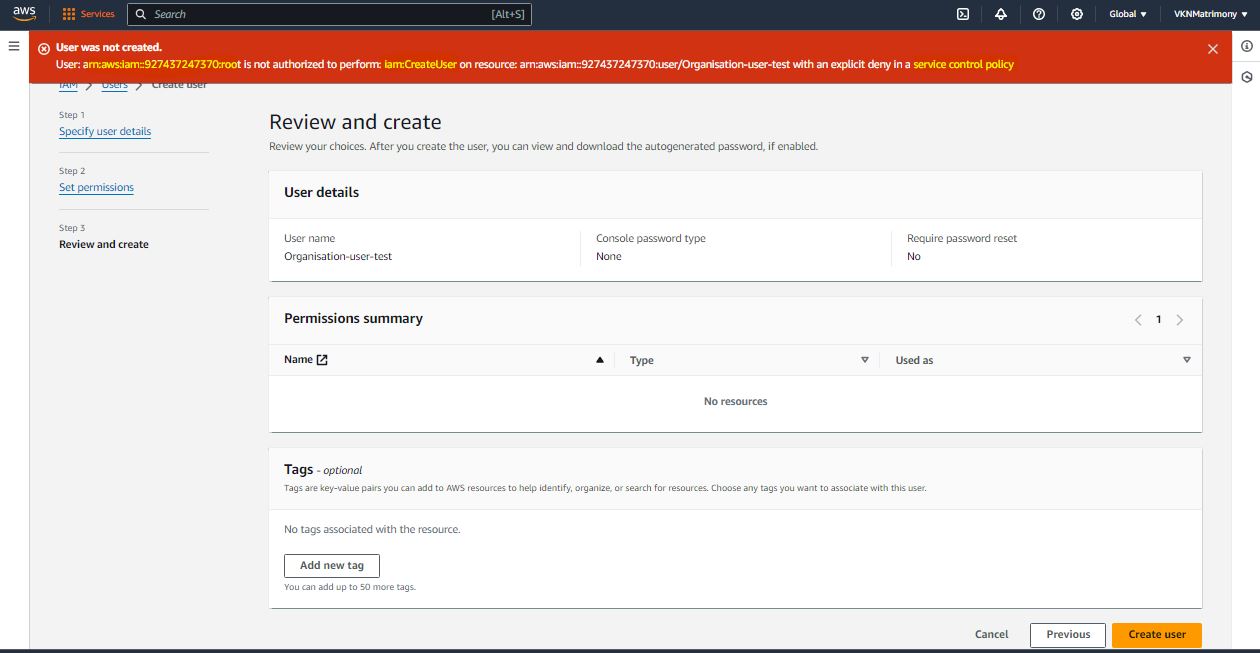
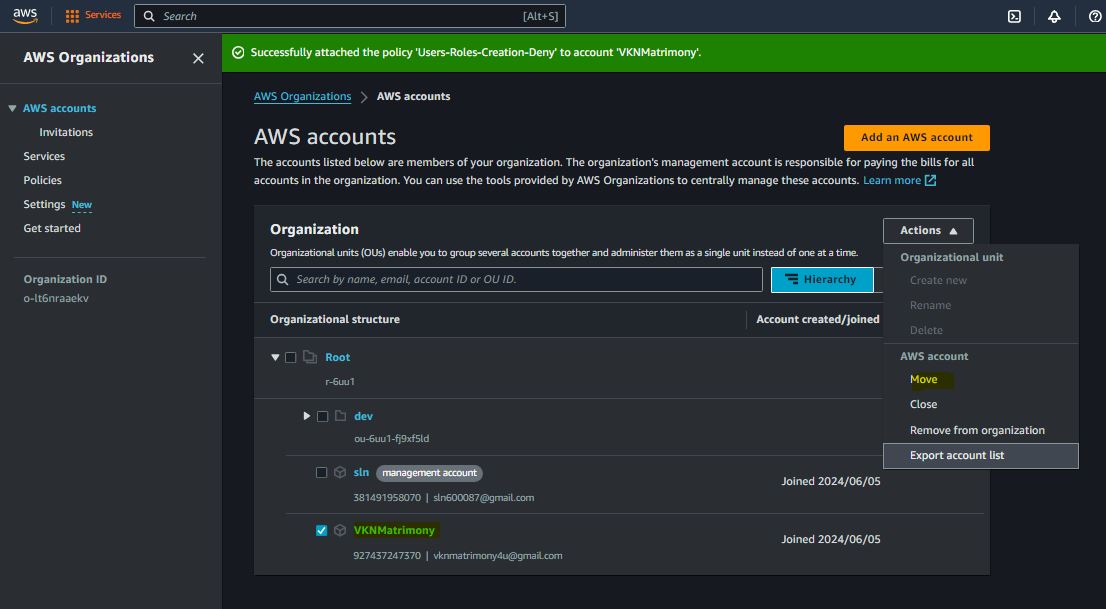
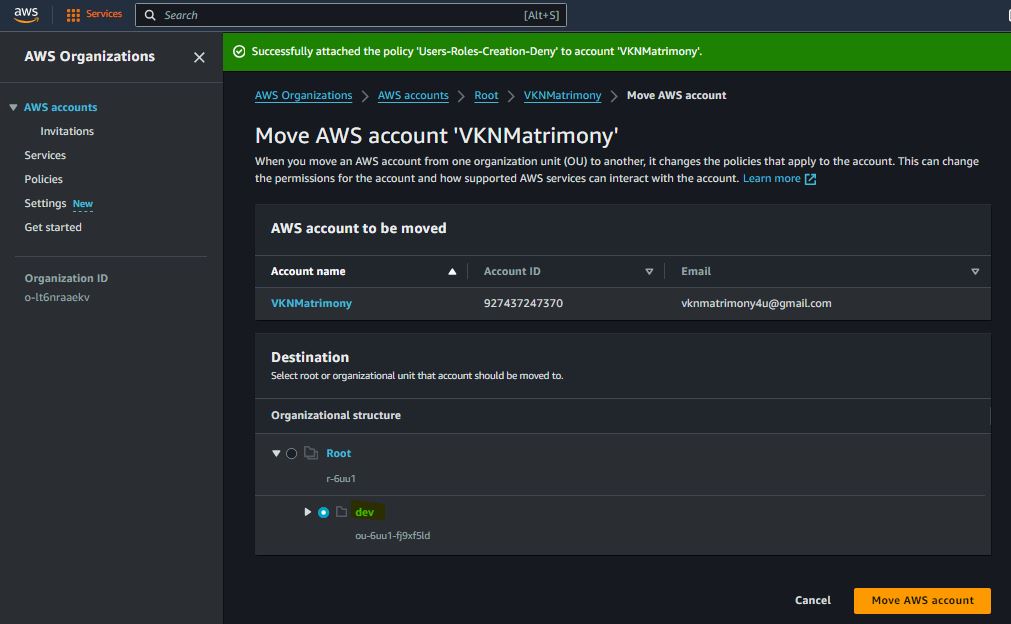
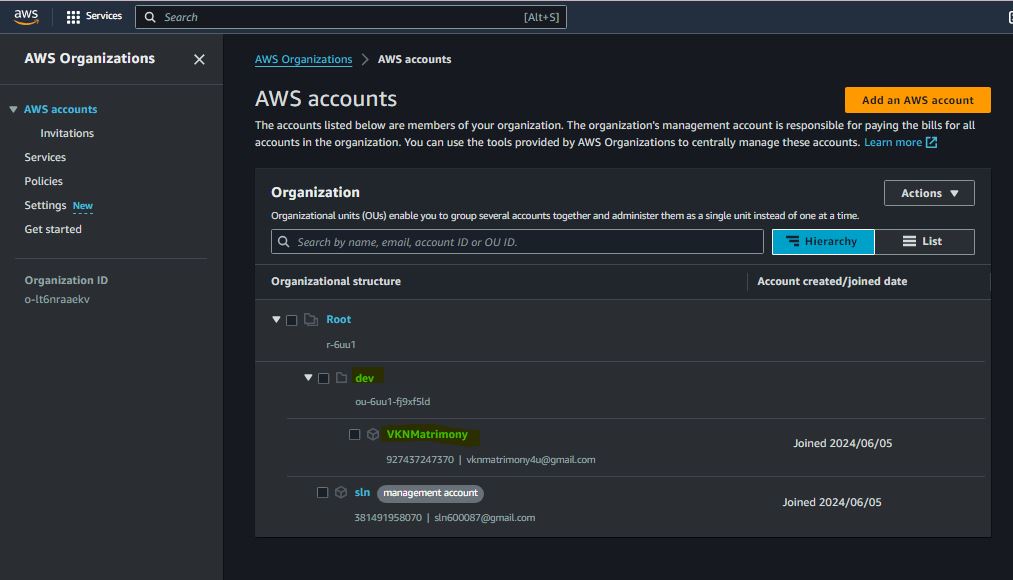
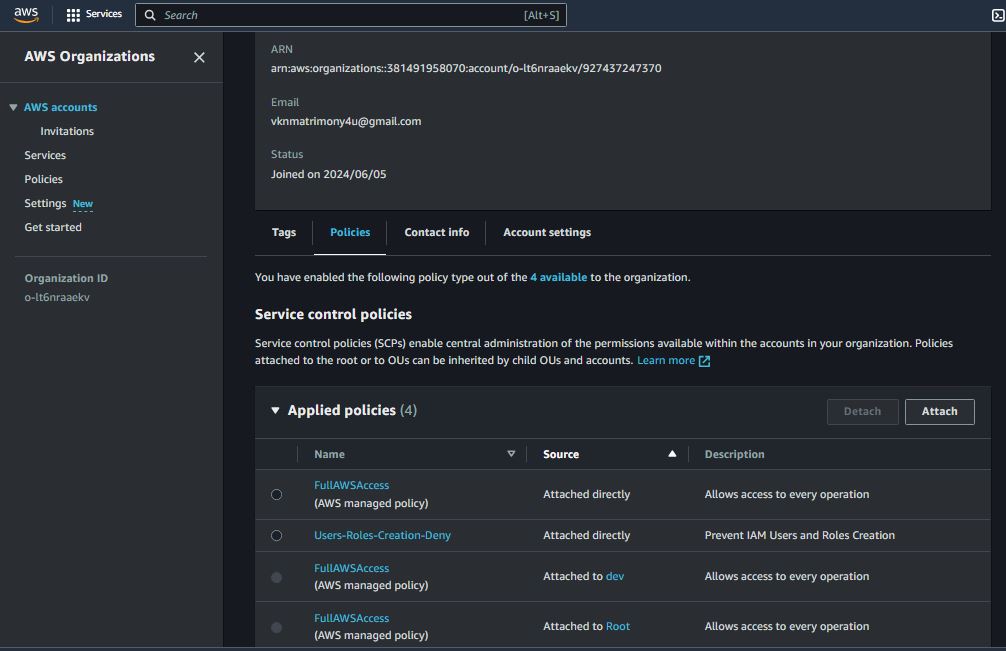
Prevent IAM Users and Roles Creation
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": [
"iam:CreateUser",
"iam:CreateRole"
],
"Resource": "*"
}
]
}
Restrict Resource Creation to Specific Regions
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": [
"us-east-1",
"us-west-2"
]
}
}
}
]
}
Prevent Deletion of Specific Resources

{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "kms:ScheduleKeyDeletion",
"Resource": "*"
}
]
}
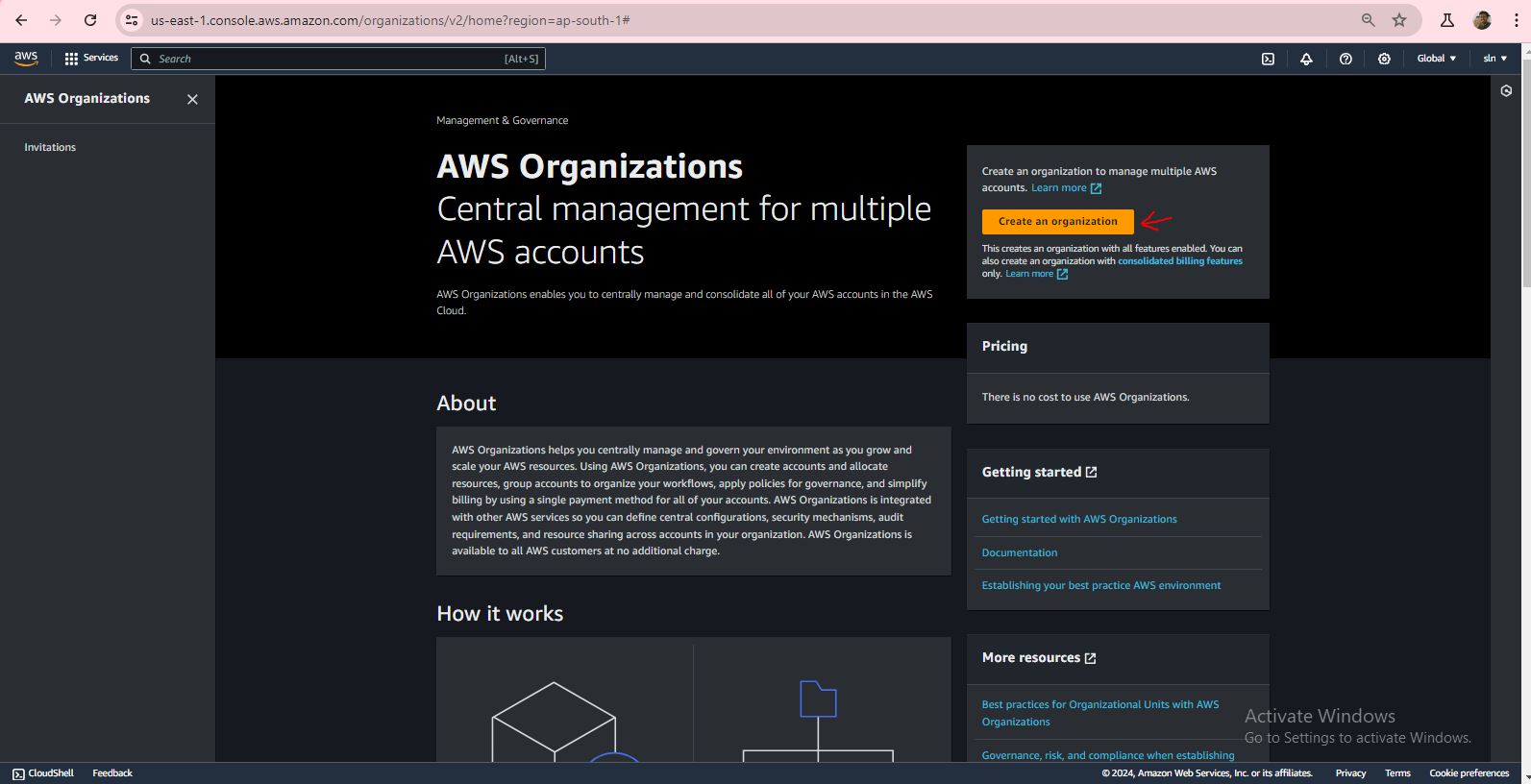
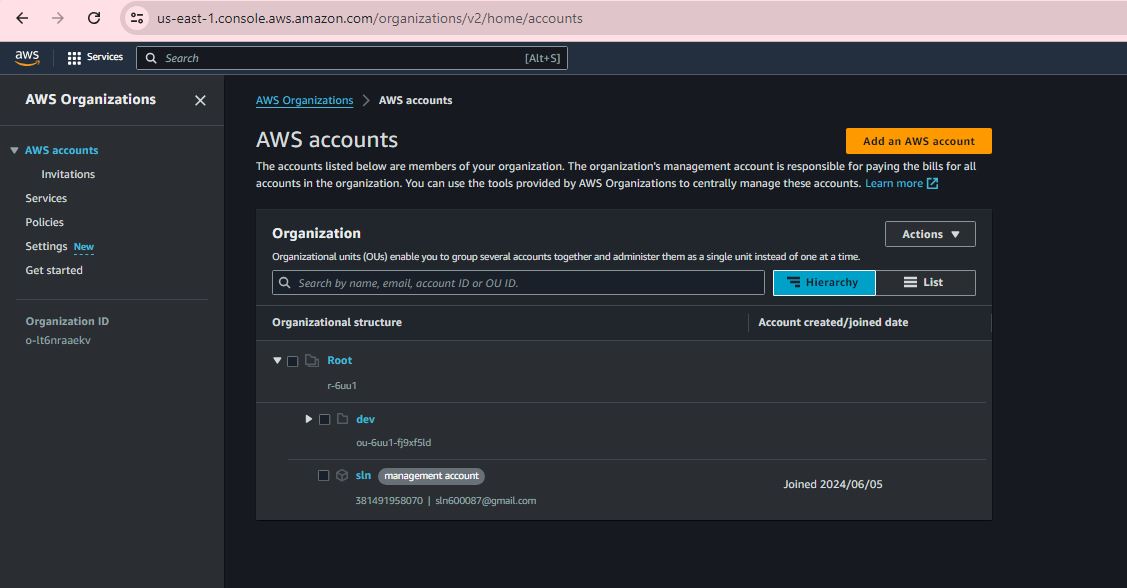
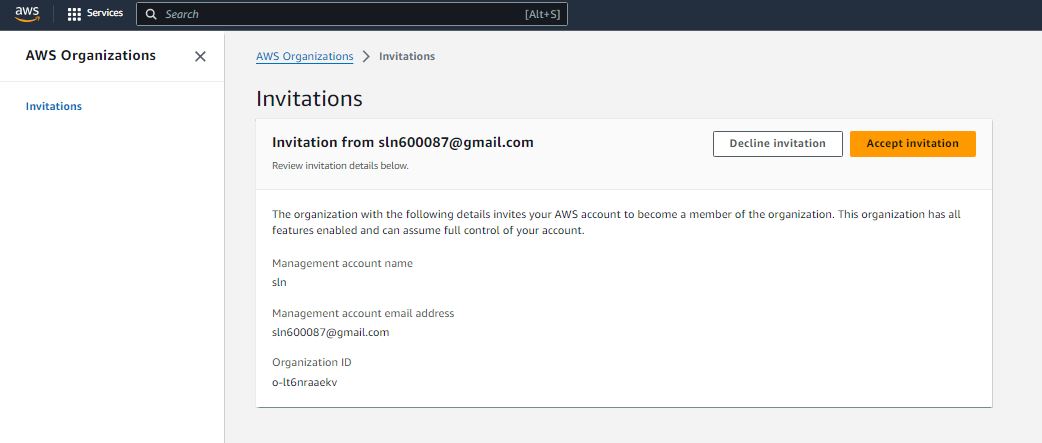
Step 1:

Step 2:

Step 3:

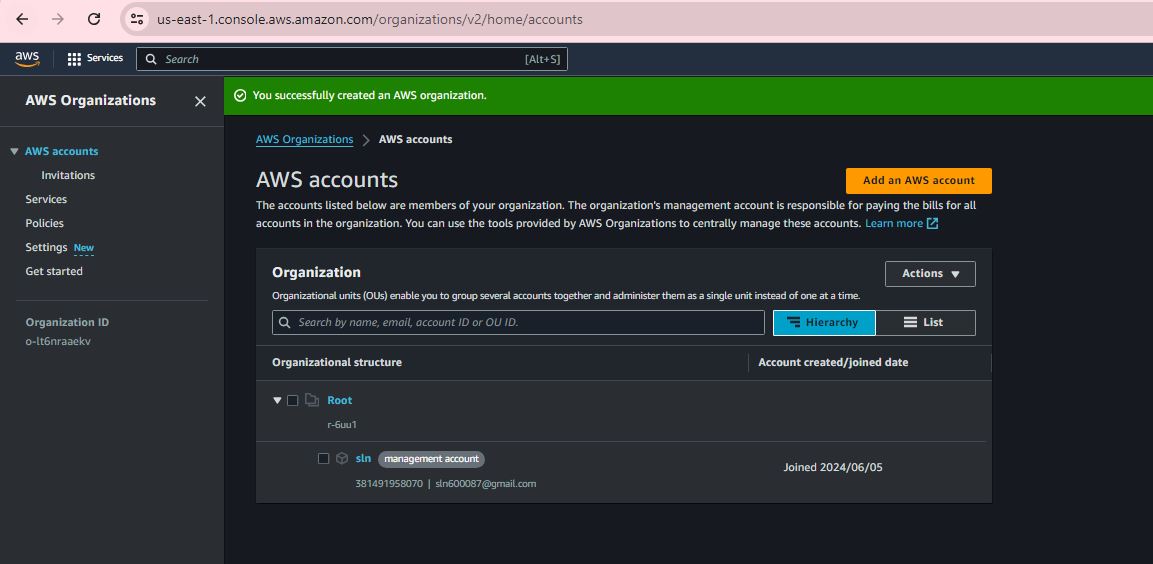
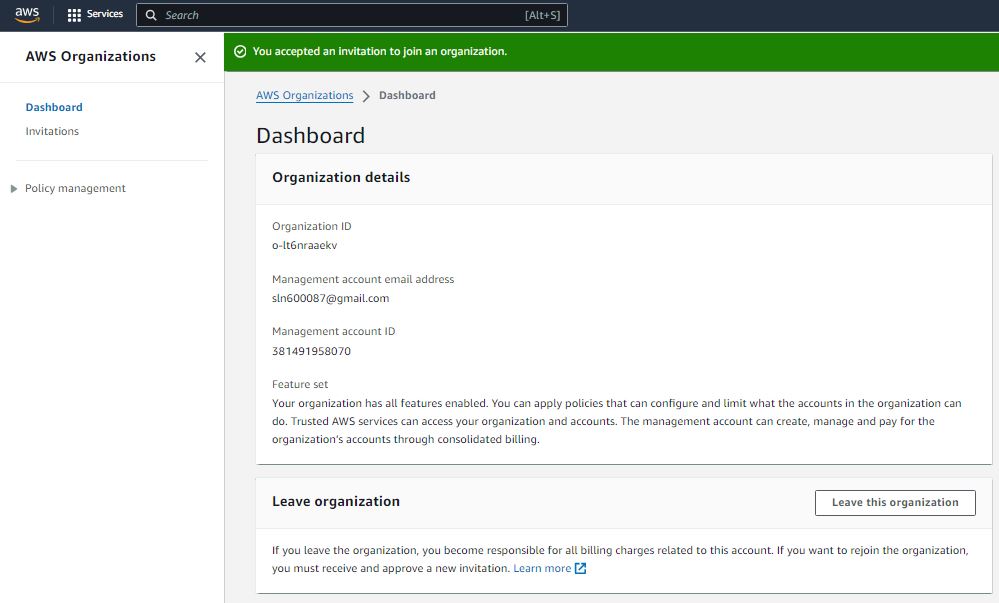
Step 4:

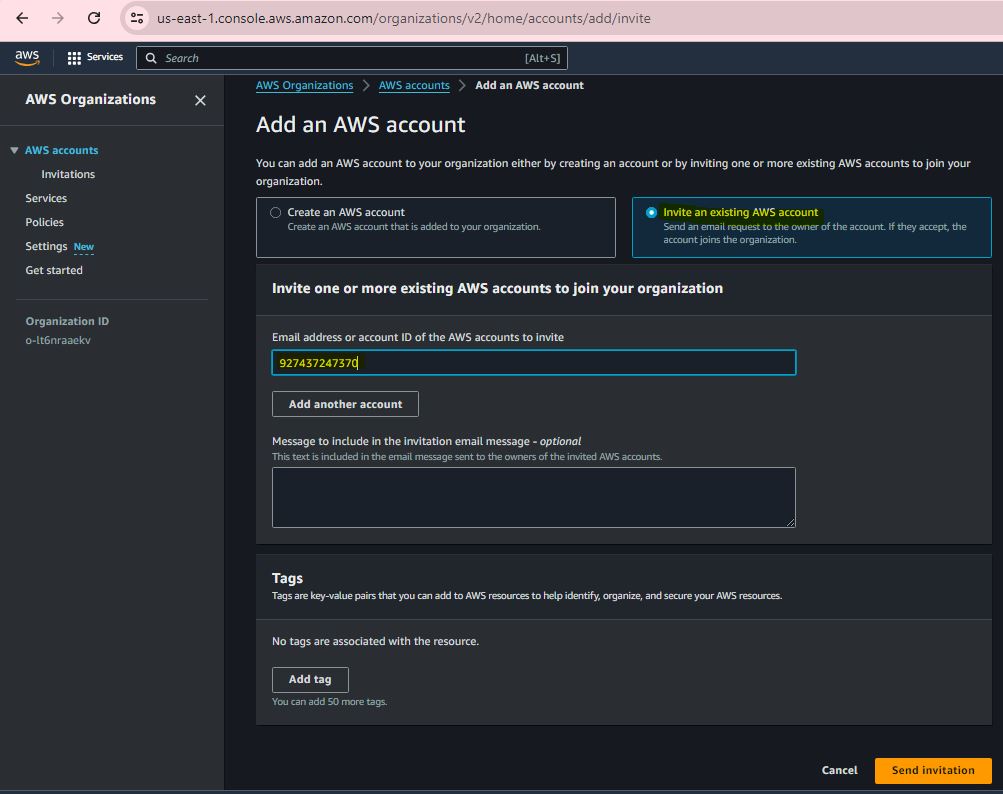
Step 5:

Step 6:

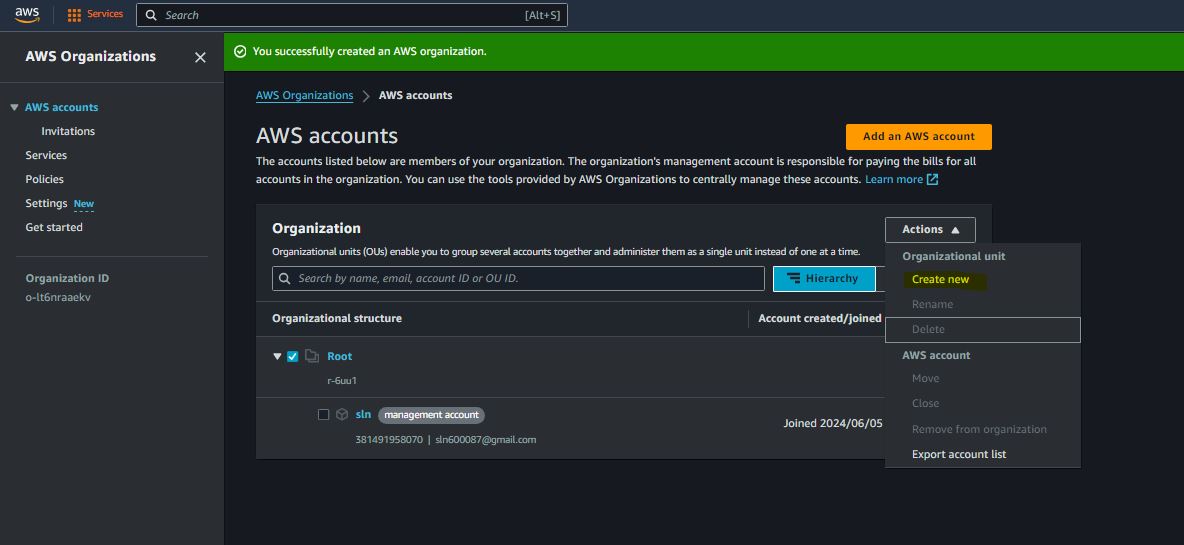
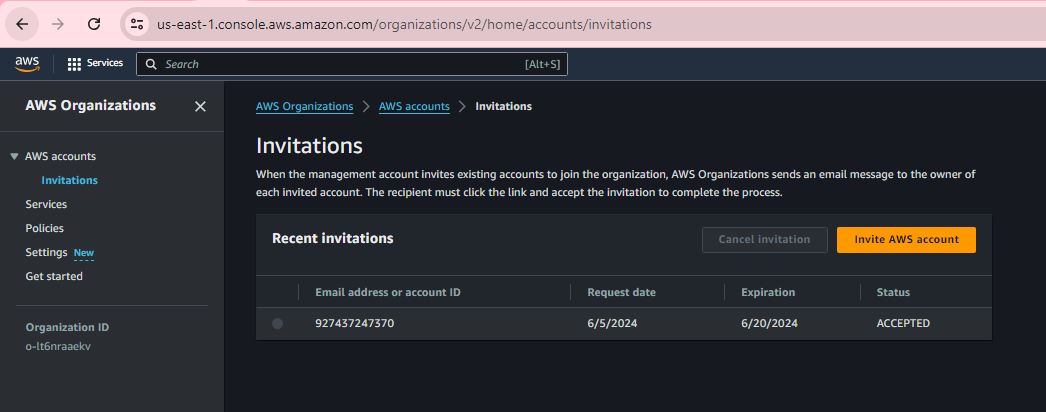
Step 7:

Step 8:

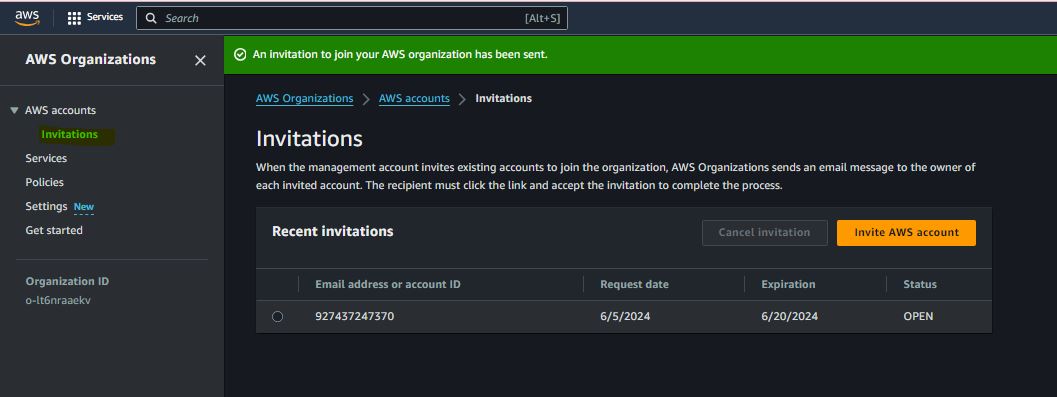
Step 9:

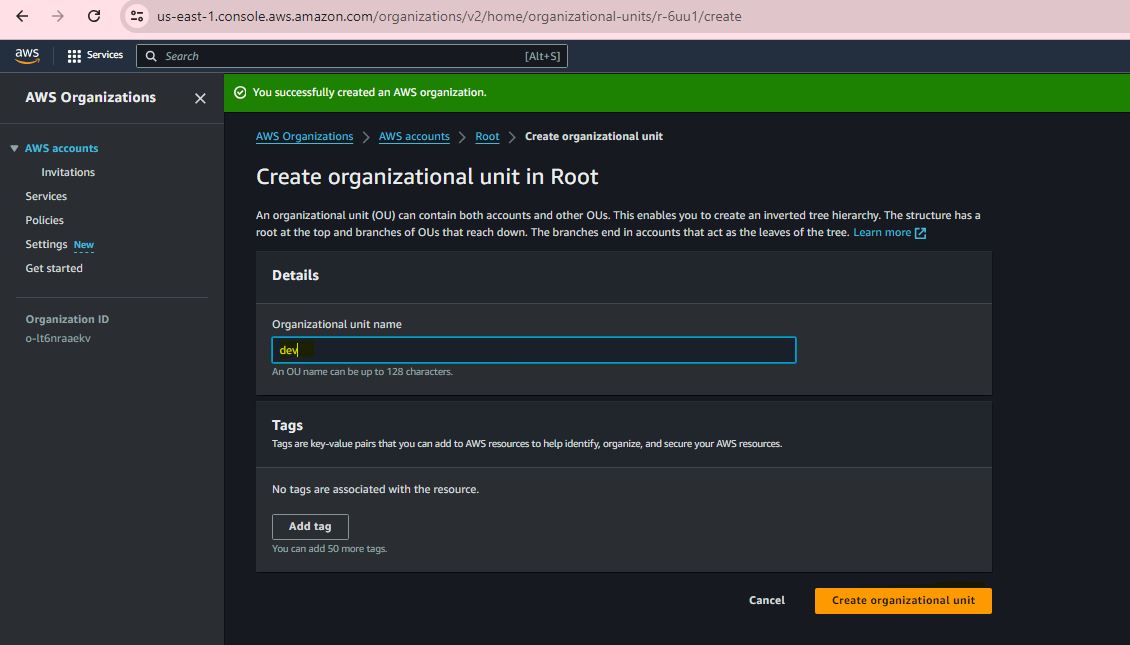
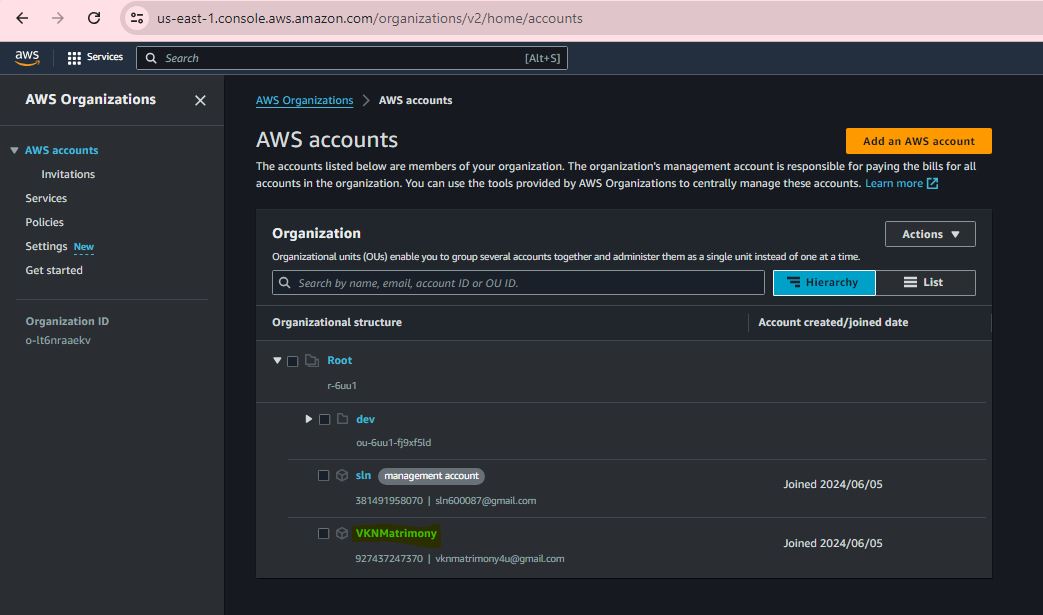
Step 10:

Step 11:

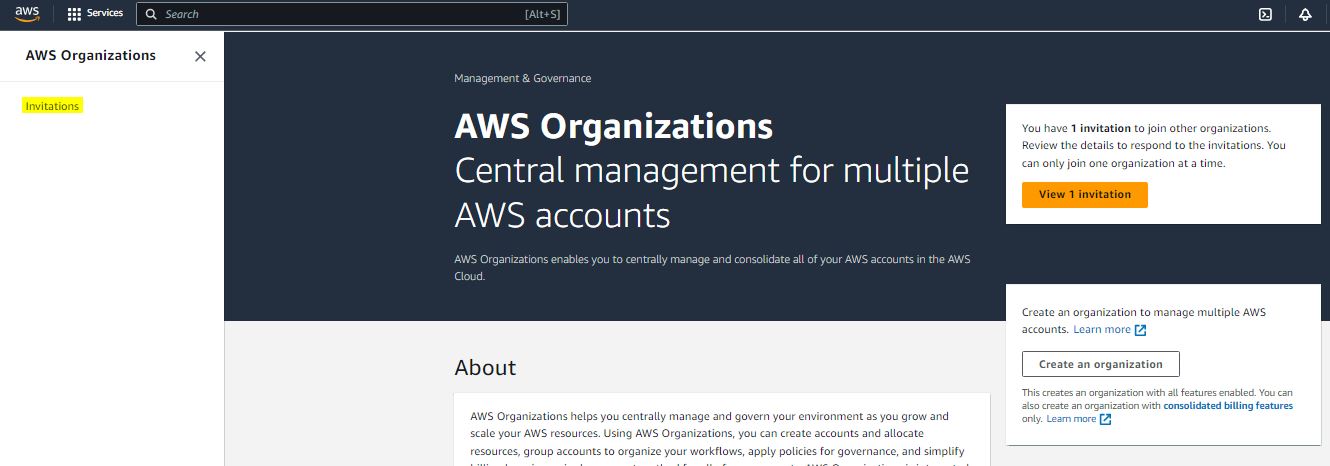
Step 12:

Step 13:

Step 14:

Step 15:

Step 16:

Step 17:

Step 18:

Step 19:

Step 20:

Step 21:

Step 22:

Step 23:

Step 24:

Step 25:

Step 26:

Step 27:

Step 28:

Step 29:

